Configuring email notifications and ticketing events for Graphus Alerts
This article describes how to configure email notifications and publish ticketing system events for graphus alerts.
Email notifications
Graphus will send an email notification to specified recipients when an alert is generated for a category you have selected. You can select more than one category. For example, if Quarantine is selected, an email notification will be sent to the specified recipients whenever an email is quarantined.
When EmployeeShield is selected, an email will be sent when a banner is applied to an email. If Phish911 is selected, an email notification will be sent when a user reports an email via Phish911.
Ticketing events
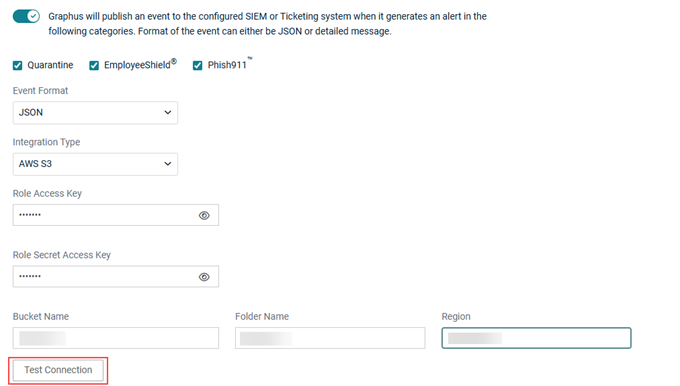
Graphus will publish an event to the configured SIEM or ticketing system when it generates an alert for the categories you have selected. You can select more than one category.
An event will be published for each category as described below:
- Quarantine: An email is quarantined.
- EmployeeShield: A banner is applied to an email.
- Phish911: A user reports an email via Phish911.
An event can be published in JSON format or a detailed message.
Integration types
Publishing an event to a SIEM or ticketing system requires that you select from the following integration types: AWS S3, Splunk, ConnectWise, or BMS. The table below describes the information you must provide for each type to complete the integration.
| Integration type | Required fields |
|---|---|
| AWS S3 |
|
| Splunk |
|
| ConnectWise |
|
| BMS |
|
How to...
- On the top navigation bar, click Insights.
- Click the name of the applicable organization.
- In the navigation pane, click Settings > General Settings.
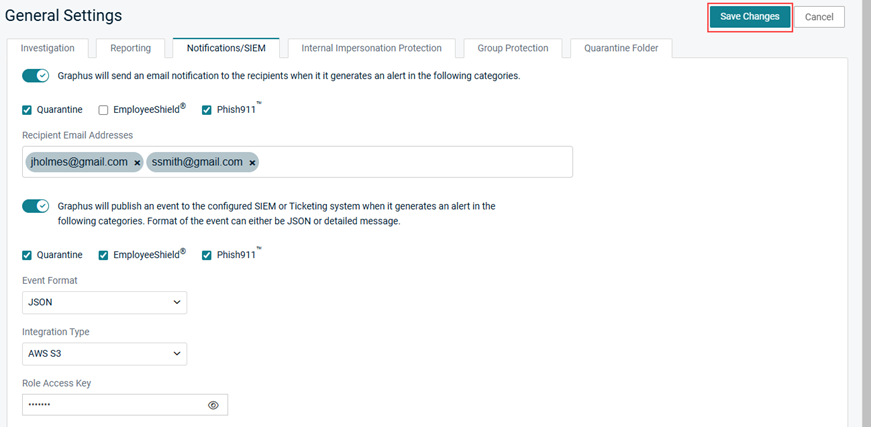
- Click the Notifications/SIEM tab.
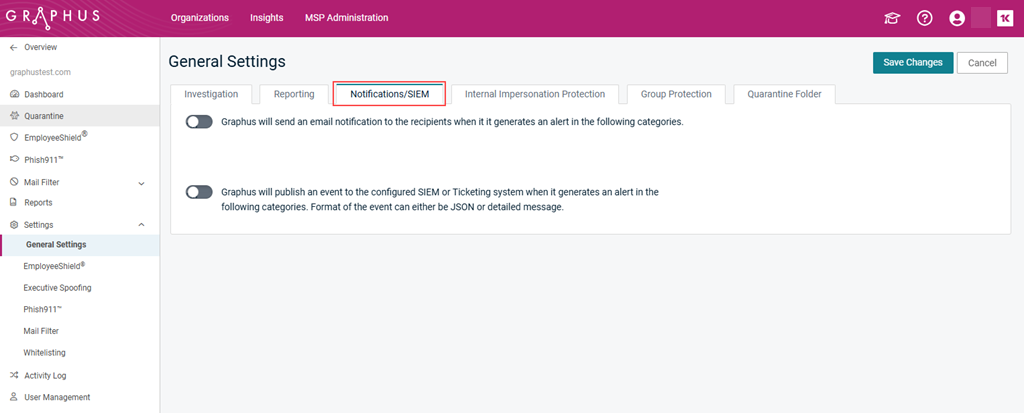
- Click the first toggle to enable it.
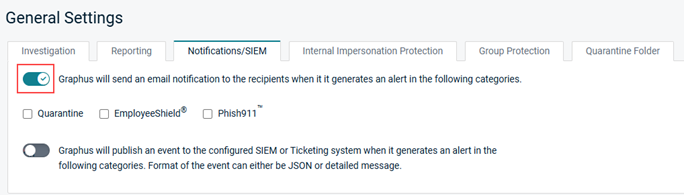
- Select the check box of each category for which you want to send an email notification.
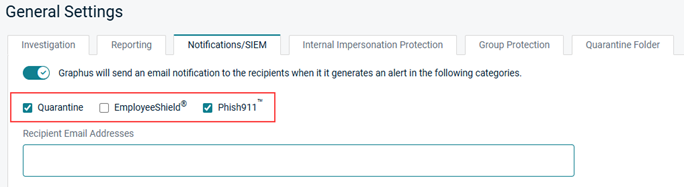
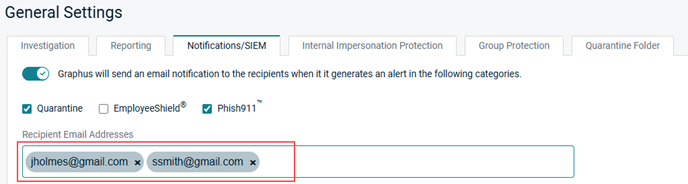
- In the Recipient Email Addresses field, enter the recipient's email address and press Enter. Repeat for each desired recipient.
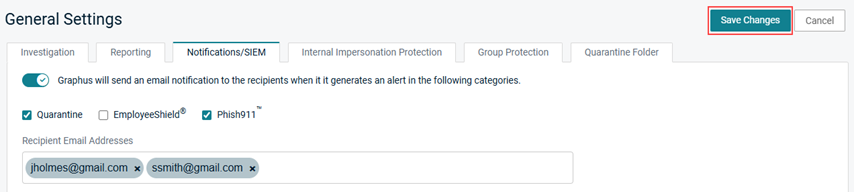
- Click Save Changes.
A message is displayed indicating the settings were saved successfully.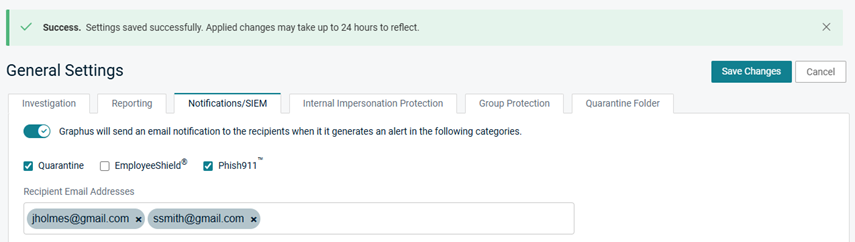
- On the top navigation bar, click Insights.
- Click the name of the applicable organization.
- In the navigation pane, click Settings > General Settings.
- Click the Notifications/SIEM tab.

- Click the second toggle to enable it.
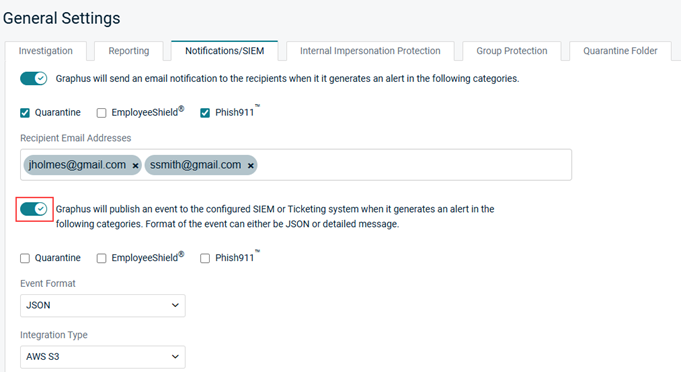
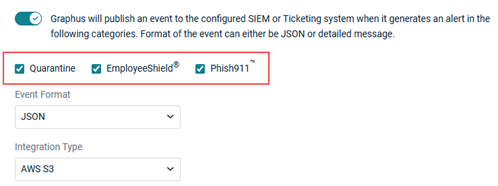
- Select the check box of each category for which you want to publish an event.
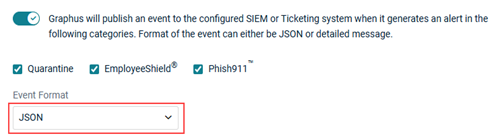
- In the Event Format field, JSON is selected automatically. If desired, select Detailed Message.
- In the Integration Type field, AWS S3 is selected by default. If desired, select Splunk, ConnectWise, or BMS.
- Complete the remaining fields based on the Integration Type you selected. See the Integration types table above.
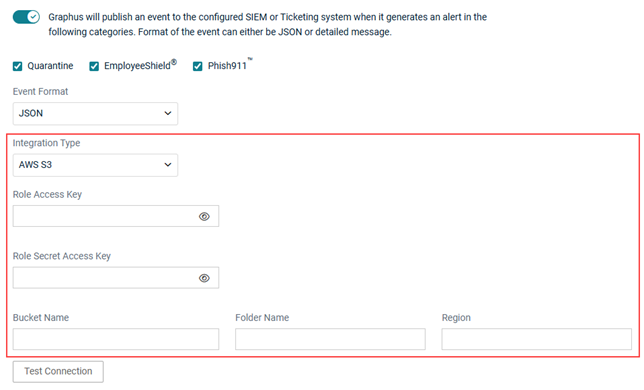
- Click the Test Connection button.
- Click Save Changes.
A message is displayed indicating the settings were saved successfully.